Within a complex and growing threat landscape, the cyber arms race is ramping up, underscoring the need for reasonable and realistic constraints on the development and use of cyberweapons. To minimize the direct or indirect harm to civilians, cyber arms development should bolster technological development safety and cybersecurity measures, and offensive cyberspace operation execution should choose the most viable course of action to achieve the specified operational effect in line with the applicable law and rules of engagement.
In this post, part of our special series on avoiding civilian harm during military cyber operations, Dr. Bernhards Blumbergs, Senior Researcher at CERT.LV (Information Technologies Security Incident Response Institution in Latvia) presents forward-looking considerations from the offensive cyberspace operation execution technical and operational perspective, based on the author’s practical experience.
Offensive cyberspace operations, such as cyberattacks, cyber-espionage, and responsive cyber-defense, are recognized by States as an appropriate option for supporting or achieving their operational objectives. This is because such operations provide a certain level of stealth, deniability, and misattribution, either used separately for conducting bespoke cyberspace operations or in support of regular kinetic forces operations.
The flexibility and asymmetric nature of offensive cyberspace operations has significantly increased the demand for cyberweapon development, leading to market saturation both from governmental programmes and increasing numbers of commercial initiatives. This, along with the seeming omnipresence of global cyber powers, may indicate a harsh tendency, where a nation-State executing cyberspace operations is likely to be conducted by employing an immensely diverse set of possible approaches against any viable target, either directly or indirectly, to achieve the defined operational effect.
Such cyberweapon developments and the conduct of offensive cyberspace operations need to be evaluated and managed to move towards avoiding unnecessary suffering and minimize the harm to civilians. This post offers considerations for shifting towards this goal, through responsible cyberweapon arsenal establishment and the conduct of offensive cyberspace operations.
Responsible cyberweapon development
Cyberweapon design and development may possess very limited restrictions for conceiving whatever is technologically possible to accomplish or support ongoing or future operational effects, while remaining aware of possible operational and legal requirements applicable to the use of the cyberweapon within the offensive cyberspace operation. Such an approach to cyberweapon development supports the free expression of thought and exploration of technological possibilities, implementing the functionality and capability technical restrictions only prior to their use in a cyberspace operation according to the applicable requirements.
The development, acquisition and containment, and arsenal maintenance for cyberweapons not yet selected for use in cyberspace operations should bolster the environmental safety procedures and cybersecurity requirements. Due to the possible technological freedom of development and the lack of initial technical limitations placed prior to their use, such cyberweapons may harness destructive power and should be contained adhering to the highest possible security measures within an isolated cyber range (ICRC report, p. 20) while under development, during controlled testing, or storage.
Such measures include the safety requirements applicable to human operators and their activities related to developing, testing, managing, and handling of cyberweapons, as well as administering the cyber range environment. In addition to heightened cybersecurity requirements, an additional layer through the establishment of red teaming and threat hunting teams should ensure a continuous active and proactive defense of the whole information system. These activities should focus on minimizing the risk of human error, insider threats, external cyberattacks, and data breaches. Notorious data breach incidents resulting in public disclosure of powerful attack and espionage tools – such as Hacking Team, FireEye red team, NSA Tailored Access Operations team, and CIA toolkit – show that even the high-profile security-focused entities may fall as victims to a well-executed cyberattack resulting in public disclosure of their cyberweapon arsenal.
Weaponization of such publicly disclosed tools and 0-days for the conduct of cyberattacks by threat actors, such as the infamous NSA EternalBlue exploit used within WannaCry and NotPetya global attacks, have resulted in global havoc, economic impact, and harm to civilians. Increased cyberweapon environment safety procedures and cybersecurity requirements should lead towards minimizing such risk and impact.
Applicable operational and legal restrictions to the developed cyberweapon should be implemented at least before their deployment and usage within a cyberspace operation, since such requirements may only be specified considering the situational context and operational needs. These technical restrictions may include the well-known safeguards (ICRC report, p. 26) such as geofencing (e.g. limiting impact to specific IP address ranges), kill-switches (e.g. limitations on specific target network environment conditions and events), and access-lists (e.g. particular identification information permitting access to the command-and-control infrastructure).
Such methods should be chosen based on the applicable legal requirements and rules of engagement, as well as considering the operational goals, such as deception, false-flag or no-flag operations, limiting attribution, or leading to a possible misattribution. Technical restrictions may be implemented at various layers: within the cyberweapon itself or in the command-and-control infrastructure, depending on the technical possibilities, operational environment conditions, and operational limitations.
Offensive cyberspace operation execution
Reaching the designated target to deliver the operational effect through the complex infrastructure of cyberspace yields an immense number of paths and approaches. This leads to a vast set of possibilities and their combinations, requiring an exhaustive and intricate analysis to identify a significantly smaller set of viable paths towards the target. Those identifying the best course of action should consider not only the operational and feasibility requirements but provide their assessment to avoid or minimize possible harm to civilians.
The difficulty of such an approach stems from recognizing a set of all applicable attack paths, analyzing their variations, and identifying the course of action to deliver the defined operational effect with the least severe impact on cyberspace ecosystem, natural environment, and civilians. An attack path consists of all technical and non-technical assets engaged directly or indirectly in the conduct of the cyberspace operation.
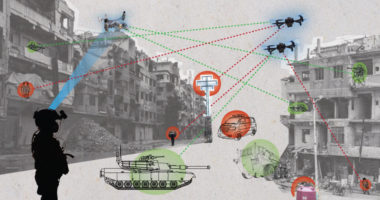
For example, a cyberspace operation to remotely control and modify the adversary’s military information system responsible for collecting and displaying battlefield situational picture at the joint operations center might depend on both kinetic and cyber engagement phases. The first phase might rely on a close-access operation requiring a physical proximity to enter the adversary’s military datacenter with a cloned access card and deploying a rogue IoT device with an out-of-band access mobile network connectivity. In the second phase, the rogue device would call back over a beacon to a command-and-control server deployed on a virtual private server in a public cloud infrastructure. Within this remote-access cyberspace operation phase, the operators would establish a connection over a chain of proxy servers to the command-and-control server allowing to use the rogue IoT device to execute a man-in-the-middle attack and inject fake information into battlefield situational picture for display at adversary’s military joint operations center.
A similar operational effect might be reached over a multitude of other paths and their combinations within or through cyberspace, potentially incurring adverse side-effects by employing methods, such as supply chain breach, remote drive-by exploit kits, or dependable system targeting. To illustrate an approach with more severe side-effects, the impact on the adversary’s battlefield situational picture at the joint operations center may be conducted by targeting the supply chain in three phases. Within the first phase, the gathered reconnaissance and intelligence information reveals that a deployed military unit in a remote mission area submits daily situational reports over a leased public satellite link. The second phase would focus on gaining access to a satellite communication provider infrastructure via targeted social engineering and spear-phishing attack campaign. Third, from the gained position, the operators may intercept and interfere with the information flows over the satellite link to deliver the specified operational effect. Unbeknownst to the operators, the targeted satellite link is also used by civilian emergency services to coordinate search and rescue operations in natural disaster-affected areas. This interference with the satellite link has a side-effect of causing disruptions to the communication channels used by emergency services and resulting in civilian casualties.
Provided examples, resulting in the same operational effect, illustrate two distinct approaches, with the first having its main effort focused on military systems with minimal impact on civilian infrastructure, and the second with the primary focus on civilian infrastructure and resulting in collateral harm to civilians.
Commanders overseeing an offensive cyberspace operation should consider possible approaches to assisted cyber-targeting and informed decision-making processes for choosing the best course of action. Such a complex task could depend on artificial intelligence-based approaches for unstructured data aggregation and parsing (e.g. data mining, and big-data analytics), attack path processing, and attack-tree visualization.
Data aggregation, mining and analysis play a fundamental part in acquiring and transforming large volumes of unprocessed and raw data into usable information. This data builds the foundation for further information analysis process and attack path representation. The variety of relevant data sources, automation of data acquisition, and the quality of the gathered data will lead to extraction of usable and sensible information and increased informed decision-making processes. Data acquisition may be considered as the hardest task to be solved, as it includes a variety of complex aspects, such as data source identification (e.g. clear-net data, vulnerability databases, data breach releases, internet infrastructure mapping data, dark-net data, geopolitical situation data, and geospatial data), automated data gathering, manual information injection and enrichment (e.g. intelligence information, and target reconnaissance information), and active scanning of network nodes.
The extracted information is further processed to create a graph of all possible attack paths, allowing the delivery of the specified operational effect against the designated target within or through a cyberspace. Within this process, the attack paths should be additionally evaluated against metrics to assign a score representing their feasibility and potential impact to civilians, internet ecosystem, and environment. Such impact score metrics may include evaluation of targeted entities, their scope of use, and criticality and significance to civilians.
The complexity of this task lies within the high computational power requirements needed to analyze, produce, and assess the whole set of attack paths and designate an impact score to every graph node and path. Based on assigned acceptable impact thresholds for the offensive cyberspace operation, the applicable attack paths are selected and visually displayed as attack trees, which would represent the ways of how a cyberspace operation might be executed. This approach would enable the decision makers to commence with an informed decision-making process towards the appropriate course of action selection for the offensive cyberspace operation with the minimal possible harm to civilians.
Takeaways and conclusions
The global cyberspace is a highly complex and intertwined ecosystem comprised of technological and human aspects. To utilize the cyberspace as a domain for operations, it needs to be fully understood and the impact of performed activities assessed. Responsible conduct of offensive cyberspace operations should consider protecting and minimizing harm to civilians.
To move towards this goal, the preparation and execution of offensive cyberspace operations should take into account the following two important considerations: 1) bolstering the security and safety measures for the cyberweapon development process and employment within an offensive cyberspace operation; and 2) using emerging approaches within machine learning, data mining, analysis, and visualization towards automating the cyberspace assessment to allow the informed decision-making process to identify viable course of action to deliver the operational effect within or through the cyberspace, with minimal possible harm to civilians, the internet ecosystem, and the natural environment.
See also
- Pete Renals, Future developments in military cyber operations and their impact on the risk of civilian harm, June 24, 2021
- Ellie Shami, Assessing the risks of civilian harm from military cyber operations during armed conflicts, June 22, 2021
- Noëlle van der Waag-Cowling, Stepping into the breach: military responses to global cyber insecurity, June 17, 2021
- Kubo Mačák & Ewan Lawson, Avoiding civilian harm during military cyber operations: six key takeaways, June 15, 2021





Hello, my question is there are any events about Humanitarian Law ?
and Thank you!
Hi and thanks Ayoub!
I would suggest you visit this page where all our law and policy public event are saved:
https://www.icrc.org/en/content/law-and-policy-events?show=past
If you are interested in learning more on IHL in general (not only with an event), you can also add the following resources:
INTRODUCTION TO INTERNATIONAL HUMANITARIAN LAW (IHL) E-LEARNING MODULES
Please find on the platform Kaya, our interactive e-learning course “Introduction to International Humanitarian Law (IHL)”. It is principally addressed to humanitarian practitioners, policy-makers and other professionals who are keen on understanding how and when this body of law applies, and whom it protects.
Once you have clicked on this link, please go to “join the course” and follow the steps to set up an account. It will only take you a few minutes.
Those modules will give you a good general knowledge of this branch of law.
IHL PHONE APP
Furthermore, we advise you to download ICRC’s new IHL Digital App here. The app gives you online and offline access to more than 75 IHL treaties, commentaries, customary IHL rules and State ratifications, in 6 different languages.
READINGS
1) The publication, “IHL: Answers to your Questions” https://www.icrc.org/en/publication/0703-international-humanitarian-law-answers-your-questions
2) The handbook, « International Humanitarian Law: A Comprehensive Introduction” : https://www.icrc.org/en/publication/4231-international-humanitarian-law-comprehensive-introduction
3) The IHL Toolkit: https://www.icrc.org/en/download/file/107723/ihl_digital-tools-handout-2019_.pdf
Moreover, we further encourage you to subscribe to our newsletter for more information on other events or trainings, promoted by the ICRC, that might interest you.